Malware (short for malicious software) is an umbrella term that encompasses many different types of malicious code including:
- Viruses
- Spyware
- Ransomware
- Adware
- Key loggers
- Trojans
- And more

Malware (short for malicious software) is an umbrella term that encompasses many different types of malicious code including:
Cloud sharing makes it very easy simple to share files (documents, presentations, spreadsheets etc). In SharePoint, OneDrive, Dropbox, Google Drive you can simply click on a document and click “share”. A link is created, which you can then copy into an email. That done, you can move on to your next “to do” without thinking about it any longer. Continue reading
Phishing is the number one method of attack for everything from ransomware to credential theft. Email phishing is the main method for delivery but other delivery means are on the rise. Continue reading
The rise in cloud services has caused a big increase in hacked cloud accounts. Compromised login credentials are now the #1 cause of data breaches around the world according to IBM Security’s latest Cost of a Data Breach Report. Continue reading
 Prioritize data security when employees leave
Prioritize data security when employees leave Businesses need to expect that one in five of their employees to leave in an average year. You can be doing all you can to retain your people, but what are you doing to protect company data when some do leave? Our eBook, 8 Steps Protect Your Company Data when People Leave explores:
Our latest eBook shares strategies to help fight employee turnover in the first place and also .
Click here to download our eBook on “8 Steps To Protect Company Data When People Leave”.

Phishing remains one of the biggest dangers to every business’s security as it is the main delivery method for all types of cyberattacks. Cisco’s 2021 Cybersecurity threat trends report shows that at least one person clicked a phishing link in around 86% of organizations and suggests that phishing accounts for around 90% of data breaches. Continue reading

Whether you work remotely or in an office, there is a fine line between personal and work tasks on a company computer. Like a lot of people that are in front of a computer for most of their work day, it is not unusual to get attached to your desktop laptop or PC. Continue reading
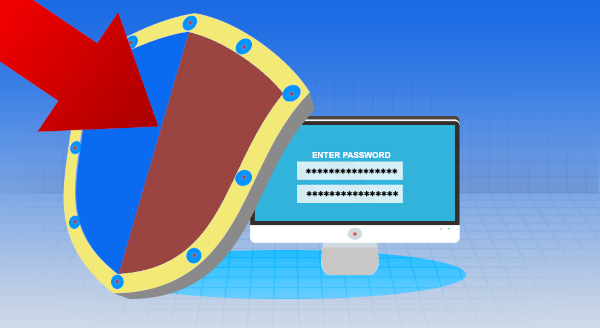
All of us like to think that we are unique and that thinking extends to our passwords too, right? We are special and distinct, and no one could guess our specific combination of letters, numbers and symbols. Well, did you know that it is very easy for computers to very quickly determine passwords. So, using a password manager is a great move, as you can securely store your passwords in an easily retrievable way. But is your master password for your password manager secure, original and long enough? Continue reading

Business downtime can be costly and there is plenty of research that show just how much it can set a business back. Some small businesses can not even bounce back due to the costs involved with an extended downtime. My latest blog article outlines the many expenses a business can encounter as a result of downtime. Continue reading
 With new cyber risks, more remote workers, and technology evolving rapidly, IT can be a lot for a small business owner to manage. Yet falling behind can:
With new cyber risks, more remote workers, and technology evolving rapidly, IT can be a lot for a small business owner to manage. Yet falling behind can:
Yet there is just so much IT! It’s difficult to keep up with it all.
Our ebook offering A framework to simplify SMB IT breaks essential skills into four key areas: Tech stack, Security and compliance, IT Management, and IT Operations. Learn what’s involved with each to improve your IT strategy.