A lot of people ask me about security and are often confused when I say you need multiple layers of security. This blog aims to explain the multiple layers and relates them to how you secure your own home or office.
Physical Security Processes
For your home or office’s physical security, you would have identified your weak points secured these with things like a fence to prevent access to your property, door and window locks and may be a dog to help prevent access.
If a burglar gets past these security measures you can use cameras, motion detectors and an alarm to warn you (or the security company) of their presence.
Once alerted you can then send around a security company to respond or call the police.
Once the threat has been neutralized, if you have any damage or have lost any property then your insurance company can help you replace these items.
Cybersecurity Processes
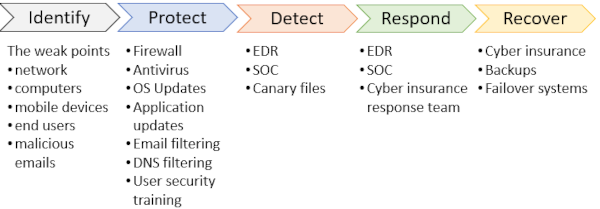
In the cyber arena a similar process needs to be followed.
Your weak points are:
- your network entry point
- all devices connected to the network (computers, phones, tablets, IOT)
- the human element.
- malicious emails.
- users browsing dodgy websites, randomly clicking on links and not following standard security principles.
To help protect these weak points you need:
- a firewall on the entry into your network
- antivirus on the devices
- you need to keep the operating systems and software update to date
- train your end users on cyber security.
- Use email filtering to remove any suspicious emails and attachments.
- DNS filtering to help prevent users going to known malicious websites.
If the bad guys get through, you need to know they are present as soon as possible:
- an EDR (Endpoint Detection and Response) software can detect abnormal processes and any other suspicious activity.
- a 24/7 security operations center (SOC) to monitor your devices and detect any anomalies
- canary files to detect if anyone is sniffing around. A canary files is a fake document used to detect if someone or something is opening or modifying your data files.
If suspicious activity has been detected you need to follow the steps of your incident response plan (if you don’t have one get one designed ASAP) which should include:
- speaking with your insurance company to get their security response team involved
- utilise your SOC (security operations center) and EDR (Endpoint Detection and Response) software to help stop and minimize any damage and then repair any issues.
Once the incident has been neutralised you then need to:
- move across to your failover systems to bring your systems up ASAP. .
- recover your data from backups.
- claim on your cyber insurance for lost business and any other remedial costs.
If you need further information or would like help on how to secure your network, then please contact DP Computing for a free no obligation chat on how we can help.