Ransomware has been a huge security threat in 2016. No-one was safe. Hackers targeted everyone and everything – including office networks and home PCs. In fact anything connected to the Internet (including smart TV’s and surveillance cameras) was fair game for them. They were very successful, with reports of upwards of $US846million reported just from incidents in the US. With this sort of monetary gain business is booming for hackers, with thousands of attacks each day bringing in an average of $US640 per target. Even more alarmingly is that the cost to the end user is on the rise with hackers demanding more and more money each time.
Some hackers even offer to help and rescue you from the issue that they caused – for a fee of course! One method is to trick you into thinking you have a virus or malware issue that will spread rapidly if you don’t pay them money to remove it. Another scarier method is that they pretend to be from a law enforcement agency (ie the Federal Police, FBI or a similar type of organisation) and say your computer was involved in a crime (anything from money laundering to child pornography). If you pay them a certain amount of money quickly you can avoid going to prison.
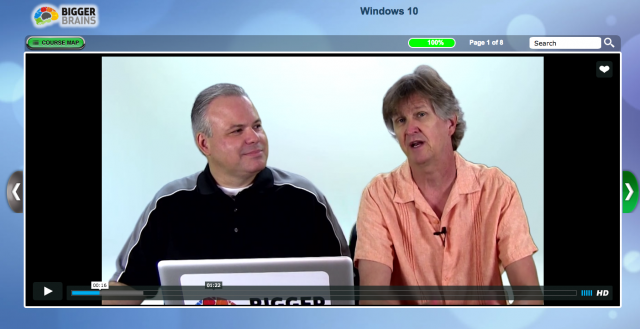
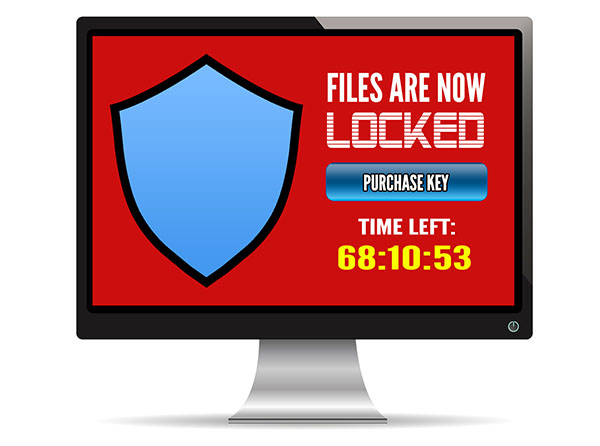
The real bad malware that is spreading rapidly at the moment are the crypto range of viruses. These viruses cause users to be locked out of their own data by encrypting files on users computers and servers. Folders of business documents, pictures, photos, music and even financial records are all held hostage until a ransom is paid. The encryption is such that it is unbreakable and unless you have a good backup paying the ransom is often seen to be the only solution.
The way these evil hackers get into your computer is deviously simple. They convince users to click on an email attachment/link or pop-up. For example you receive an email or pop up that:
- supposedly tracks an undeliverable package.
- is a bill or credit from a utility company.
- alerts you to a virus that was found and needs to be removed.
- an invoice from a company you have never heard of and / or for goods you never ordered.
- advises you of a recent traffic or some other type of fine.
They make the message so tempting to click through for more details (this is what the hackers count on). Their messages and pop-ups aren’t obvious threats and so can easily slip under our radar and through various spam and virus filters.
Paying the hackers to solve or unencrypt your files is not recommended as they are not the most trustworthy bunch. That one payment may lead to demands of more and more money with no solution in sight.
To make things worse, the malware can encrypt your backups too. Having a backup is very important in any situation, but in cases like this, the right backup is needed – with several other backup copies not connected to your network and stored safely offsite. An online backup is also recommended. Before restoring your backup remember to check that the malware isn’t lurking in the background, ready to not just re-infect your restored files but also the backup drive itself.
To avoid finding yourself dealing with ransom demands we recommend being wary of all email attachments. Even if they are from business associates, friends and family – if you are not sure what the file is don’t click it. The sender may not have sent that email intentionally and their compromised system may be automatically emailing everyone in their address book.
You should also be wary with any popups that appear out of place, especially ones that try to make you panic or do something you are wary of doing. If the message doesn’t sound or look right then don’t click it. Ransomware is just too dangerous to risk.
Also make sure your backups are working correctly and regularly test your backups.
Call us on 08 8326 4364 to set your computer up with protections against ransomware / malware / viruses, and put backups in place that will keep your important files safe.

 Every employee shares one inescapable flaw that is putting businesses at risk – they are human.
Every employee shares one inescapable flaw that is putting businesses at risk – they are human.
 One day out of the blue you receive a phone call from someone with a heavy accent (usually Indian) saying they’re from Microsoft (or some other company) or worrying pop-up appears on your screen, saying your system has been infected with a virus.
One day out of the blue you receive a phone call from someone with a heavy accent (usually Indian) saying they’re from Microsoft (or some other company) or worrying pop-up appears on your screen, saying your system has been infected with a virus. For almost a year now Microsoft has been promoting (and even pushing) a “Get Windows 10 Free” upgrade to every PC running Windows 7 or 8. The upgrade has been very controversial due to Microsoft’s aggressive tactics – a lot of our customers have found themselves “upgraded” to Windows 10 without permission!
For almost a year now Microsoft has been promoting (and even pushing) a “Get Windows 10 Free” upgrade to every PC running Windows 7 or 8. The upgrade has been very controversial due to Microsoft’s aggressive tactics – a lot of our customers have found themselves “upgraded” to Windows 10 without permission!