 The rule “If it ain’t broke, don’t fix it” is common for many business owners. It can serve to protect your business against unnecessary costs and unneeded downtime. While protecting your business against many types of danger, it poses a large threat when it comes to your IT security.
The rule “If it ain’t broke, don’t fix it” is common for many business owners. It can serve to protect your business against unnecessary costs and unneeded downtime. While protecting your business against many types of danger, it poses a large threat when it comes to your IT security.
Tag Archives: security
Don’t Be Hooked by Spear Phishing Attacks
 Phishing attacks are designed to steal your credentials or trick you into installing malicious software and still exist because they are so devastatingly simple and effective. But as with most things they evolve overtime and unfortunately become even more effective.
Phishing attacks are designed to steal your credentials or trick you into installing malicious software and still exist because they are so devastatingly simple and effective. But as with most things they evolve overtime and unfortunately become even more effective.
Is Your Actual Physical Security as Good As Your Cybersecurity?

Headlines are often made by firms that have been hacked by cybercriminals. These events sound high tech and sophisticated. The truth though is that a lot of the times it is an amateur attacker chancing their luck with an unpatched security hole or bad password. Physical break-ins though can affect businesses far more, cause much more damage and are much more common but get talked about far less. Continue reading
5 New Year’s Resolutions for Your IT Systems
The start of a new year is a great time to evaluate your IT systems and here are five great resolutions for your business to make. Continue reading
Time For A Password Refresh
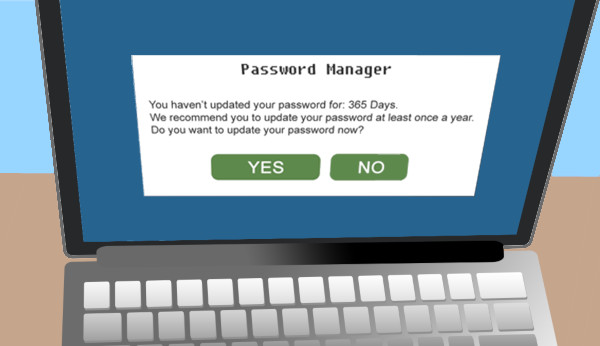
We often tend to be creatures of habit, particularly when it comes to technology and passwords are a prime example. Many people use the same password for multiple websites and applications because we don’t have a photographic memory. Most users though aren’t aware that this is one of the most significant security dangers they can face online and one with an easy fix. Continue reading
Why Hackers Target Small Businesses
Hackers today have many ways in which to attack small businesses and business owners. Many hackers attempt to gain information or attack businesses with malware, viruses or phishing attacks. One or more of these techniques can be combined with gaining physical access in an attempt to steal information and data from vulnerable firms.
This articles will help you identifying precisely how criminals target businesses to help protect you from the most devastating attacks out there.
How Safe is Your Company Data in the Cloud?
Out of all the disruptive technologies that have emerged in the last few decades, not many have had as big of an impact as cloud computing. Known by many names, this practice allows companies to store information on servers located off-premises, but are still accessible to their employees via the internet. Continue reading
Even Big Business Get Hacked! Make Sure Your Business Doesn’t Suffer the Same Fate

Up to 500 million travellers details may be compromised as hotel chain Marriott International have announced a security breach within their guest database. Researchers alerted the firm to a vulnerability that has granted hackers access to the hotel chain’s database systems since 2014. Continue reading
Common Types of Malware to Watch Out For
 What is a virus and is it the same as malware?
What is a virus and is it the same as malware?
Malware describes software designed to act maliciously on a computer. The name ‘malware’ is a shorthand for ‘malicious software’ and describes exactly what it is. A computer virus is a single type of malware that can cause harm to your PC, but it is only one of many. Other types of malware are listed below.
Adware
Short for advertising-supported software, adware is a type of malware that delivers adverts to your computer. These advertisements often pop-up and are intrusive, irritating and designed to trick you into clicking something you don’t want. A common example of malware is pop-up ads that appear on many websites and mobile applications.
Adware often comes bundled with “free” versions of software that uses these intrusive advertising to make money. Commonly it is installed without the user’s knowledge and are purposely made to be difficult to remove.
Spyware
Spyware is designed to spy on the user’s activity without their consent or knowledge. Spyware is often installed in the background, collects keyboard input and can harvest data from the computer, monitor web activity and more.
Spyware typically requires installation to the computer. This is commonly done by tricking users into installing the spyware themselves instead of a software application that they thought they were getting. Victims of spyware are often be completely unaware of its presence until the stolen data is used elsewhere (ie in a fraudulent bank transactions or stolen online accounts).
Virus
A computer virus is a form of malware that is installed inadvertently, causing damage to the computer and / or user. A typical virus may install a keylogger to capture passwords, logins and bank information from the keyboard or it might steal or delete data, interrupt programs or cause the computer to crash.
Modern virus programs commonly use your computers processing power and internet bandwidth to perform illegal tasks remotely for hackers. The first sign of this can be when the computer sounds like it is doing a lot of work when no programs are running. A computer virus is often spread through installing unknown software or downloading attachments that contain more than they seem.
Ransomware
Ransomware is a very malicious variety of malware that prevents the user from accessing their own files and data until a ransom is paid. Files within the system are often encrypted with a password that won’t be revealed to the user until they receive money usually in the form of bitcoin.
Instead of accessing the computer as normal, the user is presented with a screen which details the contact and payment information required to access their data again.
Ransomware is typically downloaded through malicious file attachments, email or through a vulnerability in the computer system.
Worm
Another type of malware is the computer worm. Worms spread across computer networks by exploiting vulnerabilities within the operating system. Often these programs harm their host networks by consuming large amounts of network bandwidth, overloading computers and using up all the available resources.
While similar to a virus a worm is able to both copies of itself and spread independently. A virus must rely on human activity to run a program or open a malicious attachment while worms can simply spread over the network without human intervention.
If you would like to make your business secure from malware, give us a call at 08 8326 4364 or via email on
su*****@dp*********.au
.
4 Ways To Protect Your Firm Against Unknown Threats
 Protecting your business against the latest IT threats should always be a top priority. Updating your antivirus and keeping your operating system and applications up to date is a great way to start. What happens though, when a threat appears at your door before security firms have had a chance to catch it?
Protecting your business against the latest IT threats should always be a top priority. Updating your antivirus and keeping your operating system and applications up to date is a great way to start. What happens though, when a threat appears at your door before security firms have had a chance to catch it?
A security threat that exploits a previously undiscovered vulnerability is known as a zero-day threat. The name “zero-day” is designed to show how long since the vulnerability was discovered and also indicates that system developers have had zero days to fix it.
A newly discovered attack might be included in a computer virus or worm. This will allow it to spread far and wide, while inflicting the maximum amount of damage possible. When spread successfully, a new exploit has the potential to reach hundreds of thousands of computers before an operating system or anti-virus update can even be issued.
Here are 4 ways to help protect your business or lessen the damage from an unknown or zero-day attack.
1. Preventative security
The number one way to mitigate the damage from any attack is to prevent it from happening in the first place. Maintaining a good firewall and up-to-date security system is the best way you can take to ensure the security of your system.
A firewall, which monitors traffic in and out of your network, reduces unauthorised entries and exits over the network. Even without knowing the exact nature of the attack, suspicious activity can be stopped.
The same is true of modern security software. Even when it can’t identify the specific zero-day threat from its virus database; it can often identify malicious intent from learned behaviour in the system.
2. A Locked Down Network
Should a zero-day threat make it into your network, our next goal is to limit its effects. By restricting user access to only essential files and systems we can limit the damage done to the smallest area. Good security policy dictates that each account should only have full access to the systems needed to complete the user’s job. For example, users from the accounts department shouldn’t have access to sales department databases – see our blog article here on this area of security.
In this way, the damage of a single compromised account is limited to only the network area it has permissions to. Limiting the impact makes it easier to recover if the worst happens.
3. Good Data backup
Whether your entire network has been exploited or only a small area has been affected; good data backups are a must and are your protection against major long term damage. Having a good backup means having the procedures in place to create regular backup copies and also regularly test those backups to make sure they can be restored at a later date.
Reliable and well tested backups are worth their weight in gold. They allow you to sleep well at night knowing your data is safe and your system can be recovered.
4. Intrusion Protection
While the precise methods of a zero-day exploit can’t be known in advance, a network intrusion protection system (NIPS) can monitor your firms network for unusual activity.
The advantage of NIPS over a traditional firewall and traditional antivirus software is that it does not rely on checking software against a known database of threats. This means it does not need updates or patches to learn about the latest attacks. NIPS works by learning the day-to-day patterns of network activity across the network.
When traffic or something out of the ordinary is detected, action can be taken to alert system administrators and lock down the network.
NIPS protects against threats introduced to the network from both external and internal sources.
Full Cover Protection
Used in combination these techniques can prevent, protect, and mitigate against the kinds of threats that even the top security firms don’t even know of yet.
If you could use help protect your business against security threats and are in Adelaide or South Australia, then give us a call today at 08 8326 4364 or via email at
su*****@dp*********.au
.

