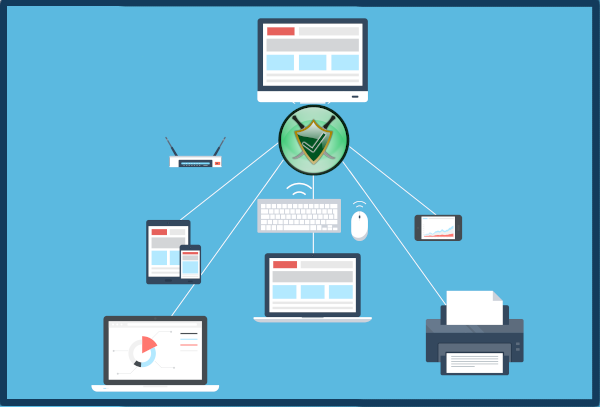
Many families today have a shared home computer to help with all their normal day-to-day activities. A teen can do school work, play games and chat to friends, a parent can check work emails, pay household bills and shop online while the youngsters play some games and browse YouTube. Yet with COVID-19 sending so many people home to work, the shared computer is getting a lot more use and is now also being used for business or corporate work. Continue reading





 Passwords are an essential part to your businesses cybersafety. If, like the rest of us, you have dozens of passwords to remember, you might take shortcuts. Taking advantage of this type of attitude is one way bad guys access your passwords.
Passwords are an essential part to your businesses cybersafety. If, like the rest of us, you have dozens of passwords to remember, you might take shortcuts. Taking advantage of this type of attitude is one way bad guys access your passwords.  Information security is on all business’ radar these days. Data drives so much of what we do. Looking to contain the risks, many sectors have established IT compliance regulations. Whether you legally have to meet a standard or not, don’t overlook these common areas of concern.
Information security is on all business’ radar these days. Data drives so much of what we do. Looking to contain the risks, many sectors have established IT compliance regulations. Whether you legally have to meet a standard or not, don’t overlook these common areas of concern.  Due diligence is about taking care and being cautious in doing business. As technology pervades most areas of business people forget that due diligence also extends to how you manage your technology! You may think you are immune to a data breach or cyberattack, but cybercriminals can target you regardless of your business size or industry sector.
Due diligence is about taking care and being cautious in doing business. As technology pervades most areas of business people forget that due diligence also extends to how you manage your technology! You may think you are immune to a data breach or cyberattack, but cybercriminals can target you regardless of your business size or industry sector.